DOI: 10.31038/PSYJ.2022432
Abstract
Civilian adaptation to a security regime supposes a calculation of costs and benefits that, being associated with adaptation to the health and economic crisis, reveal a common agenda between the rulers and the ruled. The review of the adaptation to security derived from the health and economic crises is the objective of this work. A documentary, cross-sectional and exploratory study was carried out with a selection of sources indexed to international repositories, considering the publication period from 2019 to 2021, as well as the search by keywords. The axes, dimensions, trajectories and relationships between the variables that reflect and determine the phenomenon were established. In relation to the state of the art, applications to the virtual classroom are mentioned.
Keywords
Adaptation to change, Public agenda, Health crisis, Citizen security, Biosafety and cyber security perceived by COVID-19
Introduction
Until April 2021, the pandemic has killed three and a half million in the world, although such a figure is questionable if deaths from atypical pneumonia are counted, inferred from excess mortality [1]. In Mexico, there are 600 thousand recognizable or deductible cases [2]. In this scenario, the perception of security is a central issue on the citizen agenda not only because of the health crisis, but also because of the economic crisis [3].
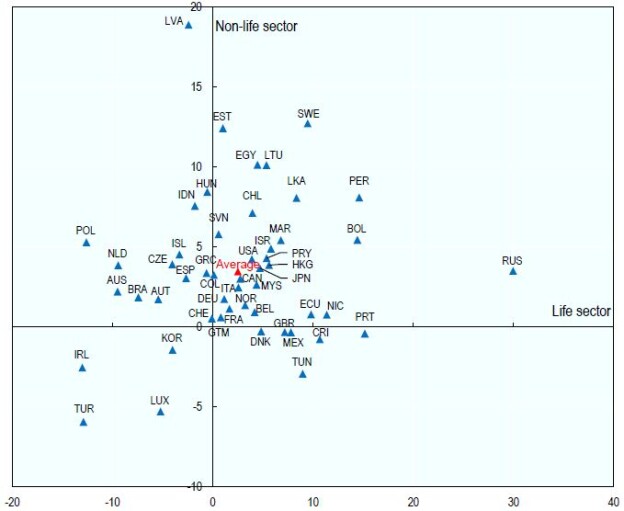
An indicator of the importance of biosecurity and cyber security is spending on insurance (Figure 1). From the year 2000 to date, an increase is seen until 2010 when a marginal decline is seen, but the date is sustainable. Mexico is located at a threshold of minimum spending on insurance against biosecurity and cyber security risks.
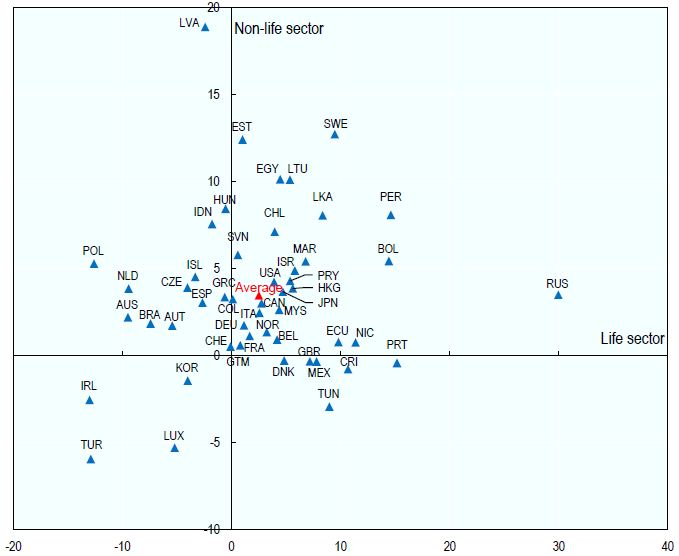
Figure 1: Insurance spending by OECD countries. Note: Prepared with data from the OECD (2021)
The United States of America is the largest insurance contractor, followed by the Japanese and the French (Figure 2). In other words, a greater propensity for risks is observed in the North American market with respect to the Asian or European one. Mexico is located in a spurious zone, very little spending on insurance relative to the OECD average.
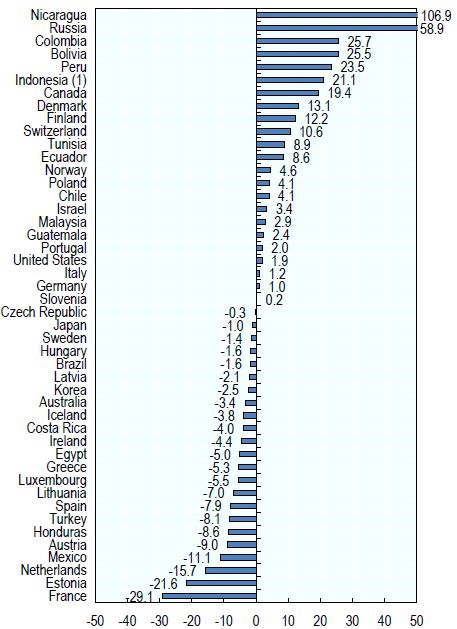
Figure 2: Figures in dollars for insurance
Other indicators associated with insurance show an increasing trend as the indicators are broken down (Figure 3). In other words, biosecurity and cyber security are transversal axes whose risk perception is observed in indicators that reflect them as central issues on the public agenda. Mexico is located in a deficit area of insurance spending compared to half of the countries that invest in insurance and belong to the OECD.
Figure 3: Biosafety and cybersecurity indicators. Note: Prepared with OECD database (2021)
In this way, the escalation of violence against vulnerable groups such as children, women and the elderly has increased exponentially and adds to the risks posed by the pandemic. Derived from this situation, the perception of security emerges, develops and consolidates as a central issue on the citizen’s agenda [4]. It is a phenomenon in which potential victims see the pandemic as unpredictable in its effects, immeasurable in its consequences, and uncontrollable by the authorities.
Such phenomena, the pandemic and security, converge in violence against vulnerable groups as a result of the frustration of family heads in the face of unemployment, hunger and poor health [5]. In this way, the areas of greatest risk are the most densely populated, such as Mexico City, mainly in the Iztapalapa mayor’s office.
Precisely, the objective of this work is to review and discuss the biosecurity and cyber security perceived in the face of the pandemic, confinement and violence towards vulnerable groups such as the elderly, women and children with respect to the head of the family, civil and health authorities, exploring the perception of security by reviewing seven dimensions: territorial, national, public (government), human, public (self-protection), private and internet user.
The discussion on the relationship between the dimensions of security has been oriented from their integration as indicators of social representation [6]. It is a process in which citizens move from the objectification of kidnappings, homicides, robberies or extortions spread in the media towards their anchoring and naturalization as risk scenarios distinguishable by sectors, zones and spaces. In other words, the fragmentation of data, images or speeches in electronic networks generates levels of security that citizens perceive as far away from worrying about their situation. Or, it assumes the risks as very close to apply voting strategies of contact with people, services or activities in unsafe areas.
This social representation of security is a framework to interpret the effects of the pandemic on the personalization of security [7]. If the media broadcast institutions, hospitals, neighborhoods and sectors affected by the community transmission of the coronavirus, then the audiences will build a public agenda segmented into dimensions that reflect their fears and expectations regarding the pandemic and its collateral effects.
What are the axes, dimensions, trajectories and relationships between the variables that explain and reflect the adaptation to the SARS CoV-2 and COVID-19 pandemic?
The premise that supports this work suggests that adaptation to change and cost benefit are the axes of discussion around the SARS CoV-2 and COVID-19 pandemic [8]. This is so because a level of social despair has been reached that translates into the establishment of an agenda focused on the use of devices outside confinement as a central strategy in the face of the health crisis [9]. By virtue of the degree of overcrowding, ventilation and stay, adaptation to change acquires levels of exposure to risk and coping behaviors in the face of the situation [10]. In this sequence of costs and benefits, the perception of risk reveals a structure of decisions and actions based on the demands of the environment and the internal resources of the civil sectors.
The contributions of the study to the discipline are 1) systematic review of the state of the art, 2) systematization of findings, 3) discussion between the findings and the literature reviewed, and 4) modeling of the variables and 5) design of pedagogical sequences. Thus, in the first section, the theoretical and conceptual approaches that explain the phenomenon are reviewed. The second section presents the results of studies related to the topic. The axes, trajectories and relations between the variables are proposed. These findings are discussed to reflect on the contribution and application of the study in the classroom.
Theories of Biosecurity and Cyber Security
In this section, the theoretical and conceptual frameworks that explain the relationship between biosecurity and cyber security are reviewed, considering their representation in the governed with respect to the public administration of the matter [11]. There are at least three phases: objectification (security as a crime prevention instrument), anchoring (crime prevention as a tool of the rule of law) and naturalization (speech attributing responsibility to the government).
Based on the three phases: objectivation, anchoring and naturalization, the theory of social representations places security as an image with meaning and a precautionary sense as long as the public administration reflects a consistent policy. This is so because citizens generate a representation of their current and future authorities based on their experiences with past authorities. This is the case of elections when voters choose the outgoing public administration based on punishment.
However, the process of representing security warns of continuous and permanent learning by citizens, as well as feedback with new symbols issued in the media and electronic networks [12]. In this way, the rulers and the ruled build a public security agenda that includes permanent and ephemeral axes and topics of discussion. This relationship between the administration of past, current and future security materializes in decisive episodes for the evaluation of the authorities and crime.
Citizens build symbols that identify their government with criminality, guiding its performance as an indicator of corruption. Or, archetypes associated with civil protection, idolizing their State as omnipresent and all-powerful [13]. In this synchrony of corruption and prevention, those who make decisions on public policies contribute to the image, prestige and reputation of their institution. If these decisions obey a synchrony with the administration of justice, then an isomorphism is appreciated. It is a transfer of government values and norms towards crime prevention that citizens value as the image of their government. This is the case of the inter-institutional coupling in matters of cooperation for the extradition of cartel leaders.
However, the theory of social representation insists that the theory of governmental isomorphism is limited in that it does not consider civil participation in the incidence of the public agenda and municipal policies [14]. In turn, for the isomorphic perspective, the analysis of the administration of power is distinctive of advanced democracies with respect to transitional political systems. This distinction suggests that advanced governance, although it includes civil participation in the corporations of order, is guided by institutional mechanisms and protocols that regulate the balance of power rather than concentrating it on an individual, group or crowd.
Meanwhile, the theory of representations suggests that, in matters of security, crime prevention and rehabilitation, the State is the guarantor of said process and the citizenry should only cooperate with the election, scrutiny, questioning, debate and establishment of a public agenda.
For its part, institutional theory recognizes that the public security administration bases its operation on isomorphism or the transfer of public policy protocols to local agencies [15]. In order to be able to guarantee the continuity of the programs, regardless of the government’s ideology, both representational and institutional approaches suggest that the crime prevention strategy be carried out. Both perspectives assume that the differences between the rulers and the ruled dissolve in the face of an insecurity problem, but they forget that the asymmetries between political and social actors intensify with the increase in homicides, robberies, kidnappings or extortion.
Both the institutional and representational views believe that the State should be the guiding axis of security, but they avoid the conflict between the governors and the governed when executing the protocols for preventing and combating crime [16]. Although an authority that is distinguished by its attention to complaints, capture of delinquents or rehabilitation of criminals generates a favorable image, it is also true that the multiplication of criminal groups is concomitant with the deprivation of liberty of their leaders.
Such issues are raised by both institutional and representational perspectives, suggesting the dissection of security by dimensions that allow anticipating risk scenarios and collaboration between the parties involved. This security governance system supposes the emergence of biosecurity and cyber security as guiding axes of the agenda, discussion, agreements and co-responsibility between public and private sectors. The way in which the relationship between the categories has been addressed is through models.
Biosecurity and Cyber Security Models
Security has been of concern to the authorities and civil society in recent years. The substrata of different societies have different perceptions about security. This, in several countries, has suffered from a lack or absence, particularly when it comes to government participation. Public security can be understood as the work of the State to protect and safeguard its population from internal dangers or threats. In Latin American countries, public custody is perceived as absent, due to the large amount of press coverage that exposes the aforementioned lack [17].
In the case of Mexico, day after day a greater amount of red news coverage appears in the news, which shows a violent face of the country. It deals with the structure of the perception of security in: Territorial security; National security; Public Safety (State as Attorney General); human security; Public security (self-protection); Private security; and, internet user perception of security, scope [18].
The literature distinguishes each of the dimensions based on observing differences between groups and people with respect to events, areas, systems or risk scenarios [19]. The common denominator lies in the calculation that individuals make regarding costs and benefits around the risks, as well as the attribution of responsibility to their rulers. In the case of the pandemic, its effects are asymmetric between those who assume that the State must manage mitigation and those who assume co-responsibility between citizens and authorities.
Public safety events like pandemics occur all over the world, posing a threat to personal safety, property, and national defense. Mexico’s security problems are similar to the general context in Latin America in many ways. However, Mexico is influenced by organized crime due to the levels of consumption of illegal products in the US market [20]. The North American drug trade, when associated with the confinement of families, fosters an environment of health risks [21].
It is stated that the perception of our reality is subjective, just as our world depends on our living conditions, operating from a higher order, a mesosystem that would include both, and in which each one appears as elements and not as closed and closed units. independent [22]. The notion that what we see might not be what is really there has preoccupied and tormented the entire population in every sector, class or role of our society. A different sector of the population would have a different expectation of security.
The administration of public security is the implementation of public policies that justify the orientation of the State in the prevention of crime and the administration of justice, but only the distrust of citizens towards the action of the government is evidenced in a growing perception of insecurity reported in literature, in seven dimensions: territorial, national, public (government), human, public (self-protection), private and Internet user [23].
Mexico can be seen from various fields such as economic, historical or social. In this sense, there are other sub-scopes ( sub-scales in the social sphere) such as health, public safety, education, environmental awareness, among others. As mentioned above, different sectors of the population have a different perception of the social sub-scopes (or subscales) [24].
From the theoretical, conceptual and empirical review, the relationships between the variables were modeled. In this way, territorial and national security are concomitant given their level of generality in the protection of the country, as well as the multilateralism involved in international or regional pacification measures. In the cases of public and citizen security, both share the imperative of safeguarding common goods that, although public, can be established as socially and environmentally available for future generations. In this sense, private and digital security are also similar in terms of preventing crimes that threaten the dignity and integrity of the individual and not of society.
The relationships between security perceptions are consistent with the observed data. This is so because the measurement of the seven security dimensions is presumed, as well as their consistency when applied to other scenarios and samples [25]. In addition, security as a multidimensional phenomenon suggests levels of measurement that are concomitant with each other, reflexive and with errors attributed to the variance of the responses.
Concomitant hypotheses refer to the covariances between the dimensions of the phenomenon, as well as to the explanation of its trajectory structure if a new specification or model were to arise when testing the null hypothesis. The reflective hypotheses allude to the relationships between the factors with respect to the indicators, suggesting the structuring of the phenomenon, as well as the convergence of the responses to the reagents that measure each feature of the dimensions [26]. Measurement error hypotheses refer to unexplained variations in the estimation of the structure of concomitant and reflexive relationships. In addition, it suggests the probable incidence of other factors and indicators not included in the model.
The theory of the perception of security alludes to converging dimensions with respect to trust between the rulers and the ruled. In this way, the central premise of the theory is that citizens have unfavorable or positive expectations of their authorities in charge of law enforcement and crime prevention, as well as social rehabilitation [27]. In this sense, security is a sociopolitical phenomenon, but reduced to media expectations of government action, as well as mistrust or empathy for its strategies, programs or policies in terms of safeguarding the integrity and dignity of its governed, as well as private property and public interests.
The dimensions of this perception of security have been structured in socio-spatial terms such as the territory or in social issues such as the nation, but with emphasis on the situation of sectors, strata or groups such as the so-called citizens and citizen security, as well as particular interests such as private and Internet security [28]. In the case of cyber security, the discussion lies in the protection and safeguarding of identity and personal data.
However, the dimensions of security converge in cyber security. The unconfirmed information disseminated on electronic networks about the risk events associated with climate change and the pandemic have generated an area of study concerning the infodemic [29]. In this way, territorial and national security have traditionally been the perspectives most approached from the sociology of risk to account for the impact of climate change on sea level and coasts, as well as risk events derived from droughts, frosts, fires, floods or earthquakes in vulnerable areas, human trafficking , species or the appearance of epidemics due to the invasion of animal territories. The dissemination of the media on these problems, associated with the confinement of people, has generated an oversupply of content, resulting in two logics: Verisimilitude and verifiability.
In the first case, alluding to credibility, the impact of the media and networks on their audiences and users supposes the influence of their content based on the demonstration of risks through images. Consequently, responsibility is attributed to the State to the extent that public administrations with similar risk events are compared. Such a process has been exacerbated during the pandemic with the intensive dissemination of unconfirmed notes.
Precisely, the second case regarding the verifiability of the information supposes an expectation based on the demonstration of data, but limited to the description of risk scenarios and probabilities of affectation. This is the coverage of risk events from comparatives of public policies, although reduced to trends of expert opinions.
Within the framework of plausibility and verifiability, the so-called biosafety focuses on food as the main indicator of the level of health in the face of a health or environmental crisis [30]. In this sense, territorial or national security should have specialized in public matters because each sector or social stratum demanded different needs according to contingent situations. Citizen security gave way to the individualization of expectations and resources, giving rise to both personal and virtual self-protection, with the emergence of cyber security.
There are more differences between biosecurity and cyber security, but both are essential for the rule of law, the administration of justice, the prosecution of crime, social rehabilitation and collective pacification. From a traditional perspective, both dimensions are observable as complementary, but from a progressive approach they are assumed to be concomitant.
In other words, the effects of climate change are increasingly linked to identity theft, extortion or co-optation, since computer crimes originate from the niches of environmental and social deterioration. Cyber security observes in real time the data of robberies, kidnappings or homicides in situations of natural disaster or health contingencies.
Studies of Biosecurity and Cyber Security
Studies of adaptation to change have focused on the validity of the instruments by estimating their internal consistency with alpha and omega parameters, as well as the adequacy and sphericity for factor analysis and structure adjustment.
Seven investigations stand out on adaptation to change in scenarios of violence and insecurity derived from geopolitical conflicts or racial cleansing, as well as immigration and human trafficking:
Mendoza et al. [31] propose the perception of territorial security as the expectations about the governing State of public peace. The variable refers to the territory protected by the State in a context where invasions extended or disappeared empires. Adaptation to change was rooted in the preservation of the territory rather than in the preservation of lineage or the prevalence of race, uses and customs, all of which were mixed with the invading culture. Only in the case of Greece, which, when invaded by Rome, not only preserved its mythology but was also plagiarized by the medieval empire.
García et al. [32] raise the perception of national security as the expectations about the State as the attorney for crimes against democracy, national identity or the interests of the population. It is a scenario of adaptation of the modern state to industrial revolutions. The identity of the State as the repository of power was in crisis and the rulers allocated their resources to the propaganda of a national identity and union in the face of invading forces. The preservation of the territory was no longer enough, but the construction of a common good that will differentiate one culture from another.
Quintero et al. [33] conceptualize the perception of human security as expectations generated before crime prevention policies, the administration of justice and the promotion of social peace. It is a conglomerate of humanist approaches from which the center of the universe is no longer the nation state but rather the individual with values and idiosyncrasies that little by little will generate sufficient intellectual capital as a weapon for the accumulation of state power and resources.
Carreón et al. [34] suggest that the perception of public security refers to the expectations that citizens generate from distrust of the State and alienation with its security institutions, while interest is focuses on civil self-protection resources. The advent of civil rights and with it the new relationship between State and society directed the concern to an internal issue. The internal affairs of the nation state were now on a public agenda after the expression of sectors and no longer in the wishes of the ruler.
Mejía et al. [35] point out that the internal perception of security refers to the expectations that Internet users consider generated from the spy State and their search for information, selection of content and dissemination of topics. It is an agenda specialized in propaganda, anti-propaganda and against propaganda. Political and social actors debate around the surrounding information on government performance and electoral preferences. The impact of security policies on voters generates a media agenda and promotion of the party in power or the opposition.
Juárez et al., (2017, p. 23) define the perception of citizen security as the expectations regarding the State as attorney general. It is a conglomeration of social demands that the government in turn raises as central axes of its agenda, but based on the expectations of voters or the proximity of the elections. Unlike internal security, where the main thing is to obtain votes, propaganda aimed at civil security emphasizes national identity in the face of crime.
García et al. [36] warn that the perception of private security refers to the expectations of civil society generated from the State as incapable of preventing crime and fighting corruption. Even organized civil sectors state that the problem lies in the State as the rector of security, since it is pragmatically related to the citizenry based on the propaganda of fear of crime.
The studies confirm the factorial structure of the perception of safety, although the research design limits the findings to the research sample, suggesting the extension of the work towards the expansion of the factors. The adjustment values and residual parameters used led them not to reject the null hypothesis regarding the significant differences between the theoretical relationships established in the literature with respect to the empirical relationships found in the study.
Method
A documentary, exploratory and cross-sectional study was carried out with a selection of 100 references alluding to biosecurity and cyber security during the period of the pandemic from November 2019 to May 2021, considering the search by keywords in the Google repository (Table 1).
Table 1: Descriptives of the sample
|
Abstract
|
Repository |
Author |
|
Shows |
Instrument |
Trajectory |
| e1 |
Academy |
Mueller |
2021 |
71 references |
Biosecurity and cybersecurity inventory |
Cyber biosecurity ← biosecurity
|
|
e2
|
Copernicus |
Pieralisi et al., |
2021 |
20 references |
Biosafety Inventory |
Biosafety ← cyber security |
| e3 |
Dialnet |
Elgabry |
2020 |
6 references |
Biocrime Inventory |
Biocrime ← Biosafety
|
|
e4
|
Ebsco |
Salem & Jagadeesan |
2020 |
13 references |
Biosafety Inventory |
Biosafety ← Institutional coordination |
| e5 |
Latindex |
Gomez et al., |
2020 |
15 references |
biosecurity inventory |
Biosafety ← Standards
|
Note: Prepared with study data
The Systematic Review Inventory was used, considering five extractions of findings qualified by expert judges in the axes, themes and discussion categories in three rounds. The first phase related to the qualification of the contents (1 for dominant biosecurity, 2 for hegemonic cyber security and 3 for prevailing cyber biosecurity). The second round refers to the feedback between the judges, after a comparison report of averages with their scores from the first round. The third instance related to the reconsideration based on the comparative data of the second phase.
The data was processed in the statistical analysis package for social sciences (SPSS version 20), considering the parameters of normal distribution, contingency and probability proportions in order to achieve a model of structural equations to observe their axes, trajectories and relationships in around biosecurity and cyber security with respect to the five selected extracts.
Results
The values of the parameters of normal distribution, contingency and probability ratio suggest that relationships prevail between the categories of biosecurity, cyber security and cyber biosecurity with respect to the reviewed findings. The three categories prevail as axes and are related to each other with respect to a threshold of permissible risk. In other words, the findings reflect the random effects of COVID-19 in an ordinal way as it spreads from biosecurity to cyber biosecurity (Table 2).
Table 2: Instrument Descriptives
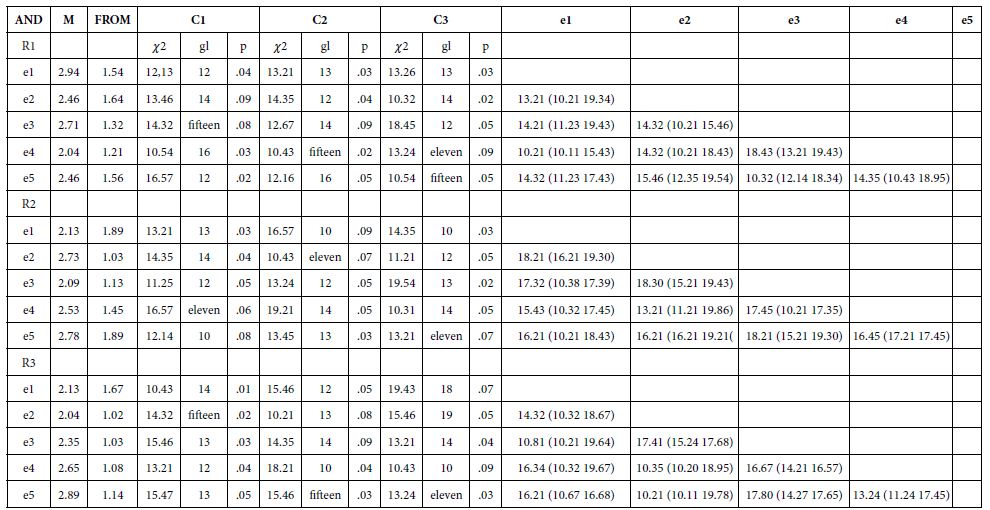
Note: Prepared with study data: E: Extract; e1: Mueller (2021), Pieralisi et al., (2021), e3: Elgabry (2020), e4: Salem & Jagadeesan (2020), e5: Gomez et al., (2020), R: Ronda, R1: Qualifying, R2: Feedback, R3: Reconsideration, C: Category, C1: Biosecurity, C2: Cybersecurity, C3: Cybersecurity, M: Mean, SD: Standard Deviation
Once the relationships between the categories and extracts were established, the structural equation model was estimated, considering the pairing between the variables (Figure 4).
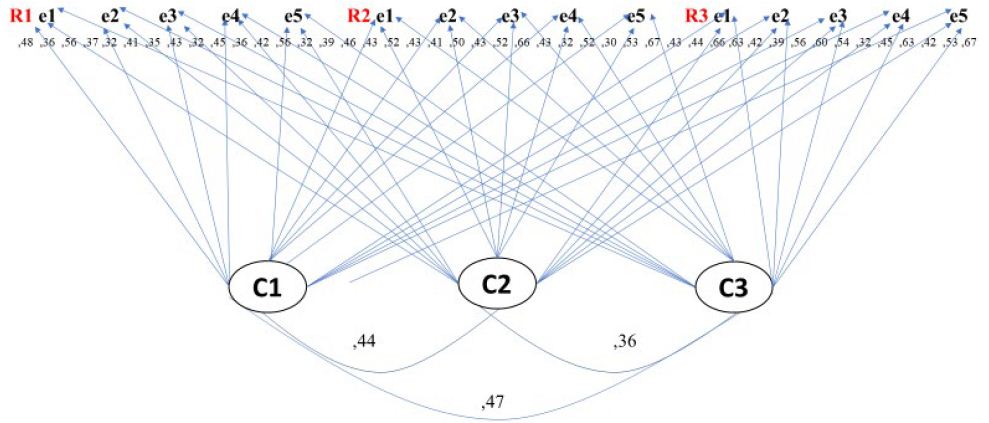
Figure 4: Structural equation model. Note: Prepared with study data: E = Extract; e1 = Mueller (2021), Pieralisi et al., (2021), e3 = Elgabry (2020), e4 = Salem & Jagadeesan (2020), e5 = Gomez et al., (2020), R = Ronda, R1 = Qualifying, R2 = Feedback, R3 = Reconsideration, C = Category, C1 = Biosecurity, C2 = Cybersecurity, C3 = Cybersecurity
The fit and residual parameters ⌠ 𝜒2 = 13.24 (14 df ) p > .05; GFI = .990; IFC, 997; RMSEA = .008 ⌡suggest the non-rejection of the hypothesis regarding the differences between the revised structure and the model established in this study. It then means that the categories and extracts configure a structure that can be established with more extracts as long as they allude to the relationship between biosecurity and cyber security.
Discussion
The contribution of the present work was to establish the modeling of biosecurity and cyber security, considering a review of the literature, as well as a selection of five findings that were associated with the categories, being observable a structure where these five extracts are related to the prevailing categories. . In relation to three meta -analyses of the categories in the COVID-19 era where they recognize a scarcity of studies and risks of bias in the samples , the present work has observed a subtracted structure from the qualification of expert judges in the matter.
Tarakji et al. [37] conclude that studies on the effects of COVID-19 are neither specific nor conclusive. In the present work, it has been shown that biosecurity and cyber security have been merged into cyber biosecurity as an indicator of the impact of COVID-19. Such a process can be seen in the insurance expenditure of OECD countries, as well as in the qualification that judges make of the studies related to the association between the categories.
Yu & Chang [38] showed that the literature consulted revolves around industrial biosecurity together with the use of cyber security technology. In the present work it has been established that cyber security is linked to biosecurity and even generates a new order called cyber biosecurity to explain the impact of the pandemic on information systems and public health.
Bastos et al., [39] showed that the COVID-19 serological studies reviewed have a high risk of bias. In the present work, the risk of bias is tolerable, suggesting the extension of the study to other repositories and categories of analysis. Lines concerning the reduction of the risk of bias will make it possible to notice the relationship between biosecurity and cyber security once the pandemic is over.
Lines of research related to the effects of COVID-19 on biosecurity and cyber security will allow warning of bias risk scenarios in the literature published since 2019. Such a question will allow anticipating strategies based on permissible risk thresholds when making decisions by consulting the literature. specialized in cyber biosecurity.
Conclusion
In relation to the theory of the perception of security, which proposes nine dimensions related to territory, nation, citizenship, public, private, human and internet, this work found that human security is the factor that reflects the structure of perceptual security. The lines of study referring to the dimensions of human security will allow us to notice scenarios of conflict between the rulers and the ruled, as well as the emergence of citizen and private security.
Regarding security studies where a continuous coercive and persuasive State stands out in its relationship with citizens, this work has discussed human security as a dimension that explains the differences and similarities between the rulers and the ruled. The development of this dimension will allow us to notice the transition from a coercive system to a persuasive one. That is to say, the security attributed to the legitimate violence of a democratic government will be observed up to the security that demarcates the regime from all responsibility and burdens the citizen with the attribution of prevention by confining their expression and their property.
Regarding the seven dimensions of the perception of security, the present study has proposed that these explain the variance and warn of the appearance of a common factor that the literature identifies as second order. The lines of research on the emergence of this common factor will allow evaluating, accrediting and certifying the relations between rulers and rulers in matters of multidimensional security.
Perceived security is a multidimensional psychological phenomenon since it derives from the relationships between authorities and citizens with respect to crime prevention, the administration of justice and social rehabilitation, although other dimensions such as sectoral or media security to explain the impact of policies, strategies and programs on civil decisions and actions.
In Mexico, a common interpretation or idea of which country lacks security prevails. The absence of custody is influenced by the presence of organized crime, the illegal sale of drugs and weapons, and the corruption available in each branch of government, among the main aspects.
The correlations of reliability and validity when the unit shows so far that there are other dimensions linked to the construct. In this sense, the inclusion of self-control explains the effects of state propaganda in crime prevention, law enforcement, and peace education on the lifestyles of civilian sectors [40-45].
Studies on citizen security identify government expectations as the predominant factor that explains the phenomenon as an efficient, effective and effective institution, but in this paper the emergence of this phenomenon has been demonstrated from a structure of perceptions around the personal, citizen, public, human, national and territorial agenda.
References
- World Health Organization (2021). SARS CoV-2 and Covid-19 coronavirus statistics. Geneva: WHO
- Pan American Health Organization (2021). SARS CoV-2 and Covid19 coronavirus statistics. New York: PAHO
- Aguilar JA (2021) Social work towards a network of violence. Research Advances.10: 1-5
- Molina MR (2021) Compare a model of security perception in the Covid-19 era. Journal of Community Medicine and Public Health. 8: 1-6
- Carreón J, García C, Blanes AV (2018b) Networks of violence around the governance of public security. Social Sciences. 4 : 60-65
- Hernandez J (2020b) Specification of a model of sexual violence. british journal of Medical and Health Science. 2:1-4
- Sandoval FJ (2020) Labor expectations in the face of risk events and collateral social effects. International Journal of Humanities, Social Sciences and Education. 7:1-7
- Garcia C (2021) Perception of security in the face of the pandemic caused by the SARS CoV-2 coronavirus and the Covid-19 disease. Epidemiology International Journal. 5:1-8
- Hernandez J (2020a) Specification of a social intervention model against Covid-19. Biomedical Journal of Scientific and Technical Research. 26: 62-65
- Garcia C (2020a) Specification of a model to study risk perception. Reget. 24: 1-8
- Garza JA, Hernandez J, Carreon J, Espinoza F & Garcia C (2021) Contrast of a model of the determinants of tourist stay in the Covid-19 era: Implications for biosafety. Tourism and Heritage. 16 : 1-13.
- Carreón J, Bustos JM,Bermúdez G, Espinoza F & García C (2020) Attitudes towards the pandemic caused by the SARS CoV-2 coronavirus and the Covid-19 disease. Invurnus. 15: 12-16.
- Nájera M, Bustos JM, Carreón J & García C (2020) The perception of risk in university students in the face of the spread of the SARS CoV-2 coronavirus and the Covid-19 disease. Psychology. 8: 94-107.
- Bustos JM, Garcia C & Juarez M (2020) Perception of security against Covid-19. Academic Research Without Borders. 13: 1-26.
- Molina HD, Garcia ML, Garcia ME, Carreon J & Garcia C (2020) A statistical approach to the behavior of the Coovid-19 outbreak in mainland China. Tepexi. 7: 6-16.
- Molina MR, Coronado O, Garcia C & Quiroz CY (2021) Contrast a model security perception in the Covid-19 era. Journal of Community Medicine and Public Health Care. 8: 77-83.
- Rincon RM, Juarez M & Garcia C (2018) Interpretation of speeches around the mobility habitus to reveal the meaning of public transport. Margin. 90 : 1-13.
- Bustos JM,Ganga FA, Llamas B and Juárez M (2018) Contrast of a prospective decision model and implications for a university governance of sustainability. Margin. 89: 1-16.
- Garcia C (2020b) Specification of a model for the study of insecurity systems. Global Journal of Management & Business Research. 20 :7-10.
- Carreón J, Blanes AV and García C (2018a) Reliability and validity of a model of perceived governance of insecurity. Without Border. 11: 1-53.
- Aldana WI, Rosas FJ & Garcia C (2018) Specification of a model for the study of the public security agenda. Atlanteans. 9: 1-20.
- Juárez M, Carreón J, Quintero ML, Espinoza F, Bustos JM & García C (2017) Reliability and validity of an instrument that measures the dimension of the perception of safety and risk in students of a public university. International Journal of Advances in Social Sciences and Humanities. 11: 23-13.
- Martinez E, Anguiano F and Garcia C (2018) Governance of social works towards a network of violence. Science Learning Educational Journal. 6:1-3.
- García C, Carreón J and Hernández J (2017a) Governance of public safety. Literature review for a discussion of the state of knowledge of criminal sociopolitical identity. Margin. 84: 1-17.
- Amemiya M (2020) Retrospective meta -analysis of the random and homogeneous effect of the validity of the risk perception scale. American Journal of Applied Scientific Research. 10: 25-35.
- Rivera BL (2020) Exploratory structural algorithm of the perceived risk factor International Journal of Invention in the Humanities and Social Sciences. 10:26-30.
- Carreon J (2020) Neural networks of scenarios, phases and discourses of Internet violence. Journal of Neurology and Neuro Toxicology, 4:1-9.
- Garcia C (2019) Exploratory factorial structure of the security public. Journal of International System. 23:82-86.
- Quiroz CY (2019) Meta- analytic retrospective of transportation risk management policies in Mexico City. NetJournal of Social Science. 7: 92-100.
- Hernandez J (2019) Harassment on the Internet in the documentary and expert agenda. Asian Journal of Science and Technology. 10:1-3.
- Mendoza D, Carre ón J, Mejía S and García C (2017) Specification of a model of propaganda representations in older adults in the face of public safety. Tlatemoani . 25:21-31.
- Garcia C, Carreon J & Hernandez J (2017b) Co-management as a security device for local sustainable development. Eureka, 14:268-289.
- Quintero ML, Hernandez J, Sanchez A, Molina HD, Garcia C (2017) Model of expectations regarding public safety in microentrepreneurs in central Mexico. Borderless. 10 : 1-20.
- Carre ón J, Hernandez J, Garcia C (2017) A theoretical review for the study of the governance of public safety. Epsys , 4: 1-15.
- Mejía S, Carreón J, García C (2016) Psychological effects of violence and insecurity in older adults. Eureka. 13 : 39-55.
- Garcia C, Carreon J & Hernandez J (2016) Governance of terror to crime. Eureka. 13:168–
- Tarakji B, Alali FM, Alenzi A, Nassani MZ (2020) Systematic review with no meta- analysis of coronavirus Covid-19. Macedonian Journal of Medical Science. 30 :108-111.
- Yu H & Chang H (2020) A meta-analysis of industrial security research for sustainable organizational growth. Sustainability. 12 : 9526-9546.[crossref]
- Bastos ML, Tavaziva G, Abidi SK, Campbell JR, Haraoui LP, etal (2020) Diagnostic accuracy serological test for Covid-19 systematic review and metaanalysis. BMJ.
- Elgabry M (2020) Biocrime and Covid-19. Security and Crime Science. 19 : 1-2.[crossref]
- Gómez M, Isaza MP, Ibañez C (2020) Let’s guarantee the quality of respiratory samples to diagnose Covid-19. Nova. 18 : 93-98.
- Mueller S (2021) Facing the 2020 pandemic: What does cyberbiosecurity want us to know to safeguard the future? Biosecurity & Health, 3 : 11-21.[crossref]
- Organization for Economic Cooperation and Development (2021). Statistics insurance . Giinevra : OECD
- Pieralisi N, Souza GN, Iwaki VLC, Chicarelli M, Tolentino SE (2021) Biosecurity perspectives in oral and maxillofacial radiology in time in coronavirus disease (Covid-19) a literature review. International Journal of Odontosomatic , 15 : 77-81.[crossref]
- Salem SB & Jagadeesan P (2020) Covid-19 from food safety and biosecurity perspective. Open Food Science Journal, 12: 1-12.[crossref]