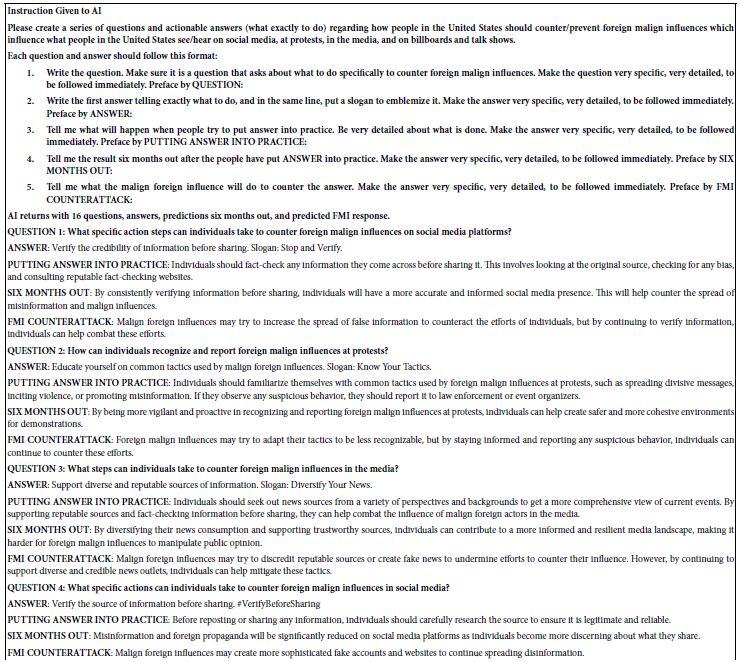
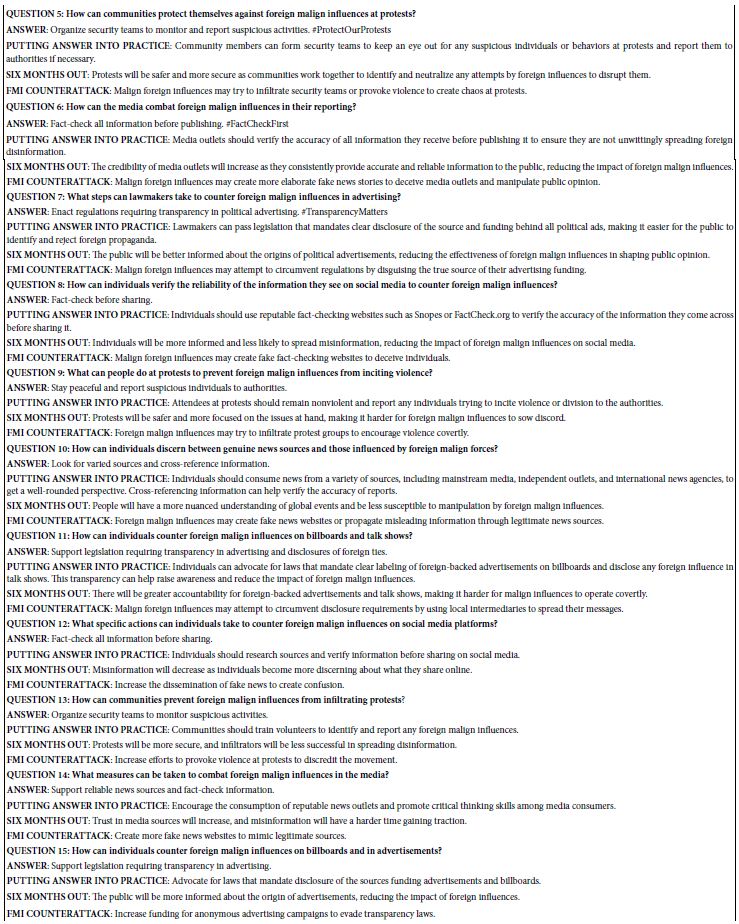
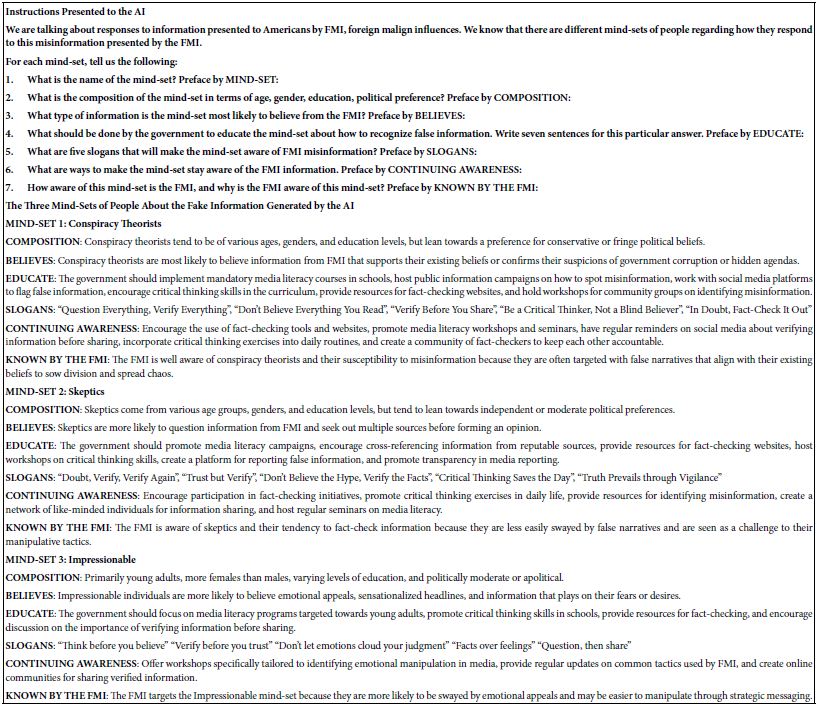
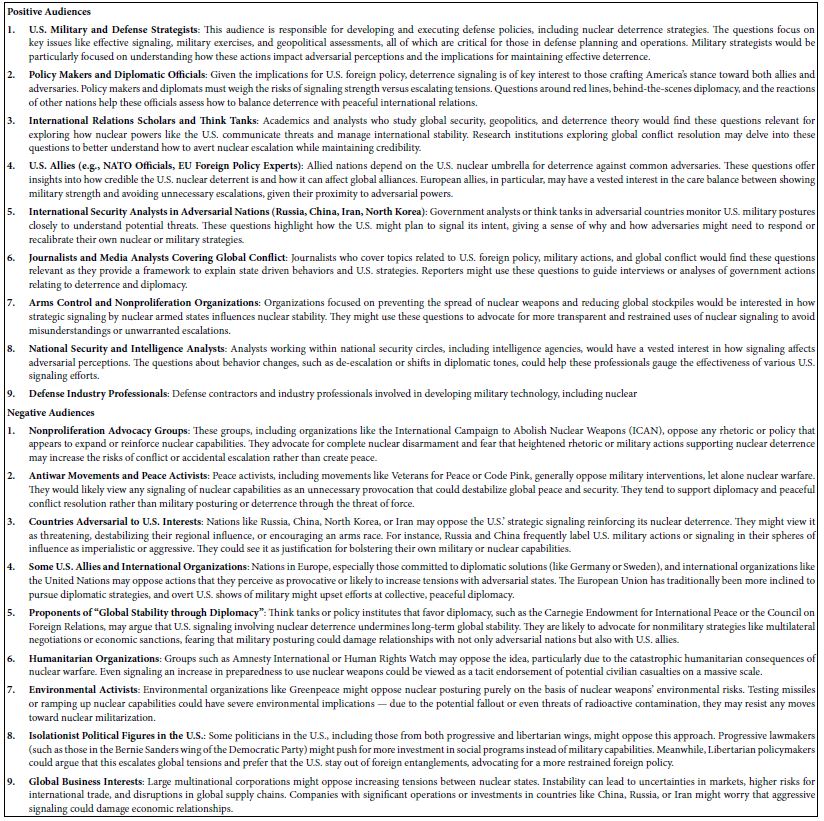
DOI: 10.31038/JNNC.2024713
Abstract
In this paper, a trans-diagnostic approach to the treatment of trauma-related mental disorders is presented. The clinical rationale for the approach is described along with several core principles of the treatment model. These include: the problem of attachment to the perpetrator; the locus of control shift; and the problem is not the problem. Rather than focusing on diagnoses, in this approach the focus is on the underlying conflicts, cognitive errors and maladaptive coping strategies. Psychiatric diagnoses are usually made within what the author calls the single disease model: in that approach there is a primary diagnosis with additional comorbid diagnoses. The assumption of that approach is that a diagnosis determines the treatment plan, and the potential treatment plans are differentiated, distinct and specific to the primary diagnosis. According to the author, however, that is not how much mental health treatment actually operates, in either psychopharmacology or psychotherapy: instead, polypharmacy is the norm, the same medications are used for a variety of different diagnoses, and psychotherapy is often multimodal and not based on any one model. For trauma-related disorders, the author advocates that the ICD-11 concept of complex PTSD should apply to the majority of cases. Rather than a diagnosis of DSM-5 PTSD with comorbid diagnoses, treatment is designed to address a poly-symptomatic trauma response that spans many DSM-5 categories. Rather than focusing on separate diagnoses, trauma-informed psychotherapy should address a set of commonly occurring underlying conflicts, cognitive errors and defenses.
Keywords
Trans-diagnostic approaches, Mental health diagnoses, Treatment planning
Introduction
The purpose of this paper is to describe a trans-diagnostic approach to the treatment of mental disorders and the rationale for it. The clinical rationale for the approach is described along with several core principles of the treatment model. These include: the problem of attachment to the perpetrator; the locus of control shift; and the problem is not the problem. Rather than focusing on diagnoses, in this approach the focus is on the underlying conflicts, cognitive errors and maladaptive coping strategies. No effort will be made to provide a literature review or to support the approach with evidence.
The Single Disease Model: Diagnosis Determines Treatment
What I call the single disease model dominates medicine and psychiatry. For example, a bacterial ear infection, a sprained ankle and pregnancy are biologically distinct, separate problems with different etiologies and treatments. It is possible for a pregnant woman to have a sprained ankle and an ear infection as well, but these are co-occurring diagnoses not variations on a single disorder or condition. For any presenting problem, the task of the physician is to set up a differential diagnosis and then, through history taking, physical examination and laboratory testing (bloodwork, X-rays, sputum or urine samples, etc.) to arrive at a single diagnosis. There are complex cases such as those seen regularly in ICUs in which a person has extensive comorbidity, but these are the exception rather than the rule.
By and large, distinct biological disorders, diseases or conditions have distinct treatments. That is why a single disease diagnosis has to be made by the doctor, either as a confirmed diagnosis or as a working hypothesis. When I finished medical school and started my psychiatry residency, it was evident that psychiatry identified itself as a branch of medicine: psychiatrists made a differential diagnosis then a single diagnosis, and the diagnosis determined the treatment plan. The American Psychiatric Association’s Diagnostic and Statistical Manual (DSM), from DSM-III (1980) [1] to DSM-IV (1984) [2] to DSM-5 (2013) [3], is divided into different sections such as psychotic disorders, eating disorders, substance use, mood disorders and so on. The terminology for the different sections has varied across editions, but the single disease model has dominated the organization of the manual throughout its history.
On the one hand, that makes sense: it is obvious that someone with bulimia is very different from someone with severe schizophrenia and they do not require the same treatment. When there is no extensive trauma history or comorbidity, the treatments of bulimia and schizophrenia are highly differentiated. In outpatient and private practice settings one encounters individuals for whom the single disease model fits fairly well.
During my residency years in Canada (1981-1985), individuals with substance abuse disorders were referred to specialty programs and were not treated within general psychiatry, in part because they did not require psychiatric medications unless they were in acute withdrawal. Then, within a few years, a new term appeared in the psychiatric literature on substance abuse: now we had to grapple with the dual diagnosis patient, which was regarded as a complex, challenging subset of substance abuse patients. In fact, individuals with extensive comorbidity are the norm in substance abuse populations, as I found in research I published in 1992 [4]: among 100 participants in treatment for substance use at an outpatient specialty clinic, 62 met criteria for major depressive disorder, 39 for a dissociative disorder and 36 for borderline personality disorder on a structured interview; 43 reported childhood physical and/or sexual abuse. The structured interview did not diagnose anxiety disorders, eating disorders or a wide range of other DSM-III disorders, so the research identified only a small portion of the comorbidity in the participants.
One of the main reasons for identifying a single or primary psychiatric diagnosis, I was taught in my residency, was to guide the selection of medications: for depression one prescribed antidepressants, for psychosis antipsychotics, for anxiety anxiolytics, for insomnia hypnotic-sedatives and for bipolar disorder mood stabilizers. The classes of medication matched the different sections in DSM-III. It all made sense in theory but not in practice. In practice, psychiatric inpatients were given a single primary diagnosis – even if additional comorbidity was acknowledged, it was viewed as secondary and not the primary focus of treatment.
A very short exposure to psychiatric inpatient units revealed that most patients were on multiple different classes of psychiatric medication for their supposed single, primary disorder. The single disease model did not in fact guide or determine treatment. Theory did not match reality. Polypharmacy was the norm, as it is today. It was, and still is, common for a psychiatric inpatient to be on an antidepressant, an antipsychotic, a mood stabilizer, and a benzodiazepine and to have been prescribed many different medications in each of those categories in the past.
The same thing is true for outpatient psychotherapy. There are distinct types of psychotherapy such as cognitive therapy, psychoanalytic psychotherapy, internal family systems therapy, EMDR and so on and some outpatients do get manualized, distinct forms of psychotherapy. However, none of those therapies are diagnostically specific – a cognitive therapist will do cognitive therapy for depression, anxiety, a personality disorder, PTSD, and numerous other disorders. Most psychotherapists and counselors practice a technically eclectic, multi-modal approach that varies a bit from client to client but is broadly the same. Treatment is not really determined by a single disease diagnosis, which is nevertheless required for insurance billing.
In the United States, the Food and Drug Administration (FDA) will not approve a new medication unless it has been shown to be better than placebo for a single DSM diagnosis such as major depressive disorder. In order to get published in a psychiatry journal, most research has to be about a single DSM disorder. Conferences, books and journals often identify a DSM category in their titles and most speakers identify themselves as experts on a DSM category. Experts on eating disorders, by and large, do not attend schizophrenia conferences, do not talk to schizophrenia experts, do not read schizophrenia journals and do not treat anyone with a primary diagnosis of schizophrenia. The mental health field is a collection of separate silos with minimal cross-talk.
The trans-diagnostic approach outlined in the present paper is based on my Trauma Model [5] and my Trauma Model Therapy [6] which rests on the foundation of the general trauma model.
Predictions of the Trauma Model
The Trauma Model [5] is designed to be scientifically testable and makes a series of testable predictions. For example, assume that the results of a large study in the general population were: women who met lifetime criteria for major depressive disorder were compared to women who did not; the female relatives of the depressed women had higher rates of major depressive disorder than the female relatives of non-depressed women; the male relatives of the depressed women had higher rates of alcohol abuse and antisocial personality disorder than the male relatives of the non-depressed women.
A common interpretation of these results within biological psychiatry would be that the primary cause of the depression in the women and the alcoholism and antisocial personality in the men was genetic: an inherited set of risk genes running in the affected families was expressed phenotypically as depression in the women and as alcoholism and antisocial personality disorder in the men. The Trauma Model makes a different interpretation: it is very depressing to be female and to grow up in an extended family of antisocial alcoholic men. These men will be perpetrators of neglect, family violence and physical and sexual abuse of their children. That’s what’s making the women depressed, not their genes.
These two interpretations of the data need not be mutually exclusive. The Trauma Model predicts that, for this example, and for mental disorders in general, there is a distribution of genetic risk from very low to very high. For the women in these families, the abuse, overall, is contributing much more to their risk for depression than are their genes. However, a few women will be at such high genetic risk that they will become clinically depressed even without severe trauma. It’s a question of the odds of depression; the degree of risk for it will increase with increasing trauma in large samples of women.
This prediction of the Trauma Model could be tested through adoption studies. The prediction is that children adopted at birth out of high-trauma families into low-trauma families will have a much-reduced risk for depression, PTSD, dissociative disorders, borderline personality disorder, anxiety disorders and a wide range of mental health problems. In the opposite direction, women adopted at birth out of non-trauma families into trauma families will have a greatly increased lifetime prevalence of all these disorders.
In a similar fashion, consider a large twin study of schizophrenia in which it was found that identical or monozygotic (MZ) twins had a much higher concordance for schizophrenia than non-identical dizygotic (DZ) twins. Let’s say that when the first MZ twin interviewed has schizophrenia, the other MZ twin has it 40% of the time; when the first DZ twin interviewed has schizophrenia, the other twin has it only 12% of the time. Within biological psychiatry this would be interpreted as evidence that schizophrenia has a strong genetic component.
The Trauma Model makes a different prediction: if severe childhood trauma was measured in a schizophrenia twin study, the results would be: twin concordance is highest in MZ twins concordant for trauma; second highest in DZ twins concordant for trauma; third highest in MZ twins discordant for trauma; and lowest in DZ twins discordant for trauma. Such results would support the hypothesis that the trauma is contributing more to the development of schizophrenia than the genes.
Overall, the model predicts, survivors of severe childhood trauma will resemble each other, and will have similar treatment needs irrespective of their primary diagnosis: the treatment of a woman with a primary diagnosis of bulimia and severe trauma will resemble that for a woman with a diagnosis of schizophrenia and severe trauma, and will be quite different from the treatment needs of a woman with bulimia and no severe trauma – the latter woman will fit the single disease model better than the trauma survivor with bulimia.
My name appears in the back of DSM-IV because I was a member of the DSM-IV dissociative disorders committee: I had an inside view of the process and spoke with a leader of the DSM process in between DSM-IV and DSM-5. The DSM leaders rejected the concept of Complex PTSD (C-PTSD) because it threatened the conceptual foundation of the DSM system, namely the single disease model. C-PTSD was incorporated into ICD-11 in 2019 [7] but does not appear in DSM-5 even though extensive research-supported submissions were made to the committees developing both DSM-IV and DSM-5 to include a category corresponding to C-PTSD, no matter what it was called.
The basic idea behind C-PTSD is that it is a trans-diagnostic disorder that includes features across many domains of symptoms, self-regulation difficulties and interpersonal conflicts. Within this framework, depression, anxiety, substance use, anger problems, personality disorders and PTSD symptoms are all elements of an inclusive trauma response, not of separate single disorders. C-PTSD dismantles the walls between the different DSM-5 silos and threatens the conceptual foundations of the DSM system.
Curiously, while resisting the inclusion of the concept of C-PTSD, no matter what its official title, the DSM criteria for PTSD have gradually drifted in the direction of C-PTSD without acknowledging it. Compared to DSM-III PTSD, DSM-5 PTSD includes a much greater emphasis on anger, negative cognition and mood, and interpersonal conflicts.
A Focus on Function, Conflicts, Coping Strategies and Symptoms
Within Trauma Model Therapy, the focus is not on DSM-5 disorders as such. Patients/clients do meet criteria for many comorbid DSM-5 disorders but the focus is on the person’s function, conflicts, coping strategies and symptoms. The DSM-5 disorders are not ignored, they just aren’t the focus. The goal is to reduce symptoms and conflicts while improving the person’s overall function and self-regulation skills. This does not mean that medications are irrelevant or disallowed: most people treated within my inpatient and outpatient programs for the last 35 years have been on multiple psychiatric medications at the time of admission and at discharge.
Trauma Model Therapy is evidence-based and supported by a series of prospective cohort studies [8-16]. There have been no randomized controlled trials because those would require millions of dollars in external funding, which has not been available.
Core Principles of Trauma Model Therapy
The core principles of Trauma Model Therapy include: the problem of attachment to the perpetrator; the locus of control shift; the problem is not the problem; just say ‘no’ to drugs; addiction is the opposite of desensitization; and the victim-rescuer-perpetrator triangle [6]. Here I will focus on the first three of these. The therapy is multi-modal and involves cognitive therapy, experiential groups, inner child work, self-regulation skill building, systems approaches and trauma education. Most recently, clients in an outpatient program I owned and ran for four years received a 91-page collection of lesson plans tagged to the group therapy sessions, which took place 20 hours per week. This program was discontinued due to low reimbursement rates by insurance companies combined with endless denials, appeals and administrative tasks.
The Problem of Attachment to the Perpetrator
The problem of attachment to the perpetrator is a core element of the treatment model. It is based on the fact that mammals are dependent for survival on adult caretakers for a period of time after birth that varies from species to species, and in humans lasts for years. Built into mammalian biology is a set of attachment mechanisms and processes: attachment to caretakers is built into mammalian biology and DNA and in humans is not due to race, culture, gender, IQ or personality. It is not optional and happens automatically. The human child loves and needs to be loved by his or her caretakers, who are usually the child’s biological parents but can be adoptive or foster parents. In a stable, healthy family this all works out – the child develops good self-esteem and secure attachment and is able to take risks in the outside world because there is a safe base to return to, home.
In a severe trauma family, there is a varying combination of emotional and physical neglect, physical, sexual and emotional abuse, absent caretakers, family violence and highly disturbed family dynamics. The child must and does attach to mom and dad, which I call mode A. However, another instinctual reaction is also operating – just like a withdrawal reflex when one touches a hot stove, the child fears, avoids and withdraws from the perpetrator(s), who are also the primary attachment figures – I call that mode B.
That is an impossible problem for the child to comprehend or solve: how to attach to people from whom you must run away. The survival imperative is to attach to an adult caretaker: the idea of the model is that there is an over-ride by the attachment systems. In order to survive, mom and dad must be OK and the child must be in mode A. For this to be true, a fundamental dissociation is required, not in order to protect the child’s feelings but to keep the attachment system up and operating. Bad mom and dad must be put out of sight and out of mind, at least enough to maintain attachment.
Sometimes mom and dad are present and not abusive. At other times they are absent, neglectful or abusive and the child activates mode B, but after a while there has to be an over-ride and a return to mode A. The child develops what is called a disorganized attachment style. From my perspective, this is actually a highly organized and tactical survival strategy: it solves the problem of attachment to the perpetrator, which is how to maintain an attachment to people who might literally kill you.
When the person comes into Trauma Model Therapy decades later they are taught about the problem of attachment to the perpetrator in group and individual therapy and in reading assignments. They then make a core realization: I loved the people who hurt me; and I was hurt by the people I loved. When this sinks in it leads to a lot of grief, mourning and loss – mourning the loss of the childhood I never actually had, which was a good, stable childhood. Addictions, acting out, rigid defenses and other survival strategies that worked in childhood but are maladaptive now must be unlearned and healthier coping strategies must be learned and practiced.
A related cognitive error is the belief that I must be weird, sick or mentally ill to love my perpetrators. The corrective cognition is telling yourself that loving your perpetrator proves only one thing: you are a mammal. It seems that no amount of abuse completely extinguishes the positive attachment, no matter how much it is disavowed, dissociated and buried.
The Locus of Control Shift
The locus of control shift is the second core principle of Trauma Model Therapy. Like attachment to the perpetrator, it is not based on race, culture, gender, IQ or personality – it is based on normal childhood cognition, which I call the mind of the magical child: I am at the center of the universe, everything revolves around me, and I cause everything that happens in my world. The child automatically shifts the locus of control – the control point – from inside the perpetrator to inside the self: I am bad, I am causing the abuse, it is my fault, and I deserve to be treated that way. These core negative self-beliefs get reinforced over and over by what the parents do (the abuse) and what they do not do (protecting the child and stopping the abuse), then by bullying at school, a sexually abusive coach, a rape at the frat house and an abusive partner or spouse.
This is the source of the self-blame, self-hatred and self-punishment that is virtually universal in survivors of severe, chronic childhood trauma. The paradox is that it is good to be bad: because the abuse is being caused by badness inside me, I can control it and stop it. All I have to do is decide to be a good little girl or boy, then mom and dad will forgive me and everything will be OK. The locus of control shift confers a developmentally protective illusion of power, control and mastery at the cost of the badness of the self. It also solves the problem of attachment to the perpetrator because it sanitizes mom and dad and creates an illusion that they are safe attachment figures. Thirty years later, the battered wife leaves the battered spouse shelter and returns home, vowing to be a better wife so that he won’t be so stressed and won’t have to hit me anymore. The domestically violent husband forgives her for leaving him temporarily and they enter a short-lived honeymoon phase until he beats her again.
When the client really gets it and it really sinks in that he or she is not bad and deserved to be loved and protected like every other child, that is good and relieves the self-blame and self-hatred. However, it also dismantles the illusion of power, control and mastery and throws the person into an underground reservoir of unresolved grief, loss, powerlessness and helplessness. I always say that no one in their right mind would want to go there, which de-stigmatizes and normalizes the avoidance so that we can look at the cost-benefit in the present of holding onto the locus of control shift.
The Problem Is Not the Problem
The problem is not the problem is adapted from general systems theory and family therapy. Rather than being psychologically meaningless symptoms of brain dysfunction, symptoms are viewed in the context of the person’s life story and are understood as maladaptive coping strategies that helped the person survive their childhood. Sometimes the model does not apply because the individual’s symptoms are endogenous, biologically driven and consistent with the disease model. However, in a substantial majority of cases, the author believes, the principles of Trauma Model Therapy can be applied and be helpful. It is important to avoid all-or-nothing thinking: for one person, psychotherapy is the primary intervention, and medications are adjunctive; for the next person, the opposite is true. Some clients want only medication, some want only psychotherapy, and some want a combination, irrespective of the clinician’s views. In all cases, the approach should be collaborative not dictatorial.
The assumption in Trauma Model Therapy is that the presenting problem – hearing voices, flashbacks, substance use – is a solution to an underlying problem. For example, a person drinks heavily to drown the sorrows arising from complex, chronic abuse and neglect and loss of loved ones. The problem is the grief, self-blame and lack of healthy self-regulation skills: alcohol solves the problem temporarily and is basically an avoidance strategy. The fact that alcohol works temporarily reinforces the addiction, as does the fact that the effect wears off and the person has to drink more.
Once the person makes a serious commitment to abstinence and to doing the work, the therapy can begin: that commitment is an ongoing process with fluctuating hard work and avoidance, often with temporary relapses. Once enough grief work, cognitive therapy and internal family systems tasks have been sufficiently completed, and healthy self-regulation strategies have been practiced and learned, it becomes much easier to say ‘no’ to alcohol. Simply removing the defense, addiction or maladaptive coping strategy does not solve the underlying problems: hence the concept of the ‘dry drunk’ who is still miserable and difficult to tolerate.
Rather than being symptoms of brain disease, voices are understood as arising from dissociated ego states, especially if they speak in sentences and paragraphs and converse with each other – they can be engaged in psychotherapy and participate in the work. They are holding thoughts, feelings and beliefs that have been disowned and disavowed by the person. They aren’t just symptoms to be gotten rid of, rather they are parts of the person and parts of an overall survival strategy that needs to be adjusted: it worked well in the emergency situation of childhood but isn’t working so well now.
Flashbacks are conceptualized in a similar fashion: rather than being symptoms of brain damage or dysfunction, flashbacks are an effort to review the tapes of the trauma. What happened leading up to the trauma? What red flags did I miss? If I can make a list of all the red flags, stay hyper-aroused and scan for danger, I can spot the red flags in the future and take evasive action. It is my own fault that I didn’t do so the first time (locus of control shift).
Conclusions
The author has reviewed some of the principles of Trauma Model Therapy, which is a trans-diagnostic approach to mental health problems and addictions. The assumption is that trauma in many forms is a major driver of symptoms and disorders across the mental health field, in a proportion that varies from case to case. The model provides a rationale for trauma therapy irrespective of diagnosis and provides an extensive set of strategies, techniques and interventions for the therapist [6]. Its effectiveness is supported by a set of prospective treatment outcome studies.
References
- Diagnostic and statistical manual of mental disorders, 3rd. ed (1980) Washington, DC, USA: American Psychiatric Association.
- Diagnostic and statistical manual of mental disorders, 4th. ed (1994) Washington, DC, USA: American Psychiatric Association.
- Diagnostic and statistical manual of mental disorders, 5th. ed (2013) Washington, DC, USA: American Psychiatric Association.
- Ross CA. Kronson J, Koensgen S, Barkman K, Clark P, Rockman G (1992) Dissociative comorbidity in 100 chemically dependent patients. Hospital and Community Psychiatry 43: 840-842. [crossref]
- Ross CA (2007) The trauma model: A solution to the problem of comorbidity in psychiatry. Richardson, TX: Manitou Communications.
- Ross CA, Halpern N (2009) Trauma model therapy: A treatment approach for trauma, dissociation and complex comorbidity. Richardson, TX: Manitou Communications.
- World Health Organization (2019). International Classification of Diseases and Related Health Problems. Geneva: World Health Organization.
- Ellason JW, Ross CA (1996) Millon Clinical Multiaxial Inventory – II follow-up of patients with dissociative identity disorder. Psychological Reports 78: 707-716. [crossref]
- Ellason JW, Ross CA (1997) Two-year follow-up of inpatients with dissociative identity disorder. American Journal of Psychiatry 154: 832-839. [crossref]
- Ross CA, Ellason JW (2001) Acute stabilization in a trauma program. Journal of Trauma and Dissociation 2: 83-87.
- Ellason JW, Ross CA (2004) SCL-90-R norms for dissociative identity disorder. Journal of Trauma and Dissociation, 5(3).
- Ross CA, Haley C (2004) Acute stabilization and three month follow-up in a trauma program. Journal of Trauma and Dissociation 5(1).
- Ross CA, Burns S (2007) Acute stabilization in a trauma program: A pilot study. Journal of Psychological Trauma 6(1).
- Ross CA, Goode C, Schroeder E (2018) Treatment outcomes across ten months of combined inpatient and outpatient treatment in a traumatized and dissociative inpatient group. Frontiers in the Psychotherapy of Trauma and Dissociation 1: 87-100.
- Ross CA, Engle M, Baker B (2018) Reductions in symptomatology at a residential treatment center for substance use disorders. Journal of Aggression, Maltreatment & Trauma 28(10).
- Ross CA, Engle M, Edmonson J, Garcia A (2020) Reductions in symptomatology from admission to discharge at a residential treatment center for substance abuse disorders: A replication study. Psychological Disorders and Research 28, Available from: https://shorturl.at/WGdDm